Regulation
The Latest Developments in ISPS: How AIGIS and New Screening Rules Are Rewriting Port Security
While the core essence of the International Ship and Port Facility Security (ISPS) Code hasn’t changed, the environment in which it operates is continuously shifting.
For Port Facility Security Officers (PFSO), facility managers, and anyone involved in ISPS compliance for your company, you'll have probably heard of a wave of stricter enforcement and the new possibilities of tech integrations.
In this article, we contextualize the:
- New government database for port ban lists
- Joint collaboration across all seaports, inland ports and waterways in Belgium
- Ramped up fight against organized crime at the ports
- Initiatives in other parts of Europe
We know it's a lot to keep tabs on, so we've gathered some of the major changes reshaping the port security landscape right now, both in Belgium and beyond in Europe!
1. What Changed in Belgium? A Snapshot of the New Reality
Increased Enforcement at the Ports
Between the announcement of all Belgian seaports and inland ports joining forces for integrated port security (via the Port 2 Port Security Platform) just months ago, screening initiatives by the Federal Police Service leading to the suspension of more than 300 employees at the Port of Antwerp-Bruges as reported at the start of the year, the message from authorities is clear.
They are cracking down on organised crime and cross-border threats (drug smuggling, cyber-attacks, misuse of drones etc.) at the ports.
In plain text? Authorities are now coming together to exchange knowledge on inspections, access control, security screenings, and more.
AIGIS Replaces Excel Sheets
In the past, managing port bans (a.k.a. people who are not allowed to access port facilities) was a logistical headache involving Excel spreadsheets.
Not anymore!
In case you haven't heard, the Belgian Justice Ministry has officially launched AIGIS, a centralized, secure platform that manages all judicial port bans in real-time.
"This makes it easy for port companies to check whether people are allowed access to their facilities. Security services such as the police, shipping control and customs also have access for better cooperation." - Paul Van Tigchelt, Federal Member of Parliament, former Federal Minister of Justice and the North Sea
There were 235 people on that list when it was announced in January 2025.
Automation in Compliance
If you've already been diligently checking your workers, contractors and visitors, against the AIGIS banlist, the most significant operational shift would probably have been trying to integrate AIGIS checks with your daily operations.
The good news? Technology and automation has bridged the gap! As of 2026, access management systems have begun executing these checks in real-time, removing the manual burden entirely!
"The recent revision of the law encourages an automated, structural approach and promotes the exchange of information between the authorities involved, with particular attention to protecting critical infrastructure, port facilities and personnel." - Port of Antwerp-Bruges
2. What Else is Happening in Europe?
Belgium isn't alone. Across Europe, there's been plenty of movement too.
Here are just some big updates regarding ISPS and/or port security from our neighbours and more.
The Netherlands: Secure Chain Expansion (Rotterdam)
.webp)
"Anyone who attempts to illegally collect a container from a terminal is in breach of the Port Security Act." - René de Vries, (State) Harbour Master of Rotterdam, Port Security Officer
Germany: Digital Trucker Identification (Hamburg)
.webp)
Europe Wide Initiatives

3. Back to Basics: What is ISPS Again?
Amidst these tech-driven updates across Europe, it is crucial to remember the foundation they are built on. So let's recap: the ISPS Code is the global standard set by the International Maritime Organization (IMO) to protect ships and port facilities.
Who does it apply to?
- Passenger ships
- Cargo ships ≥ 500 GT
- Port facilities serving international traffic
The Core Aims:
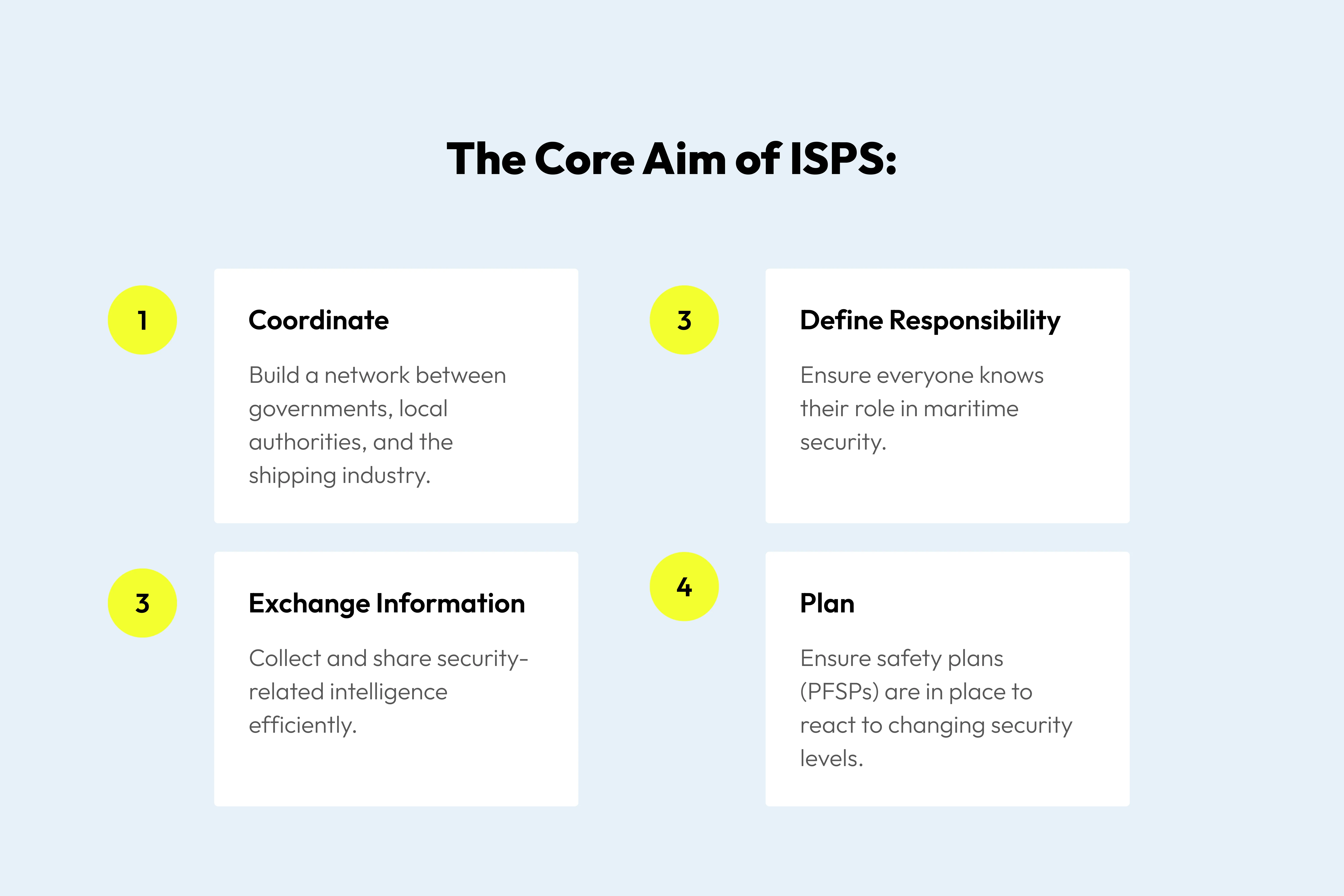
Every port facility is required to conduct at least four minor exercises and one major exercise every calendar year.
Need guidance on exercises? Check the European Handbook of Maritime Security Exercises and Drills from the Port of Antwerp-Bruges in the Further Reading section below!
4. The 2026 ISPS Compliance Checklist
With new possibilities with AIGIS integrations and stricter enforcement in Belgium, alongside initiatives rolling out across Europe, you might be wondering if your facility is keeping up.
This overview covers the six critical pillars to look at with regards to basic ISPS compliance, as recommended by the ports of Antwerp-Bruges, Rotterdam and Hamburg.
Pillar 1: ISPS Perimeter & Fence
Establish a clear boundary where security rules must be observed. The perimeter must be completely closed to prevent unauthorized access.
- Height & Construction: Ensure the fixed construction is at least 2.40m high.
- Anti-Scaling: Install anti-scaling protection (e.g., barbed wire) as an extra section on top of the 2.40m fence.
- Anchoring: Ensure the fence is buried or anchored to the ground. If not buried, fit it with an impenetrable tension wire at the bottom to prevent crawling underneath.
- Waterside Security: Ensure the fence extends to the waterside with anti-climb plates. If a physical barrier isn't possible at the quay edge, ensure appropriate human or digital surveillance is active when vessels are present.
- Action: Conduct a "walk-around" to ensure no pallets, trees, or lamp posts are close enough to the fence to act as a ladder.
Pillar 2: Gates
Gates are points of entry, not gaps in security. They must offer the same level of protection as the fence.
- Construction: Gates must be the same height as the fence. Ensure there is no gap between the gate and the fence that a person could crawl through.
- Operational State: Gates must be capable of being locked in the closed position. Gates not in use must be permanently locked.
- Lighting: Equip all operational gates with adequate lighting for night inspections.
- Signage: Install clear signage reading "ISPS Restricted Area" or "Authorized Persons Only" at every entry point.
- Action: Inspect the bottom of the gates—if there is a gap large enough for a person, install a metal bar or rubber skirt.
Pillar 3: Access Control
The process of distinguishing between 'authorized' and 'unauthorized' persons via rigorous verification.
- Mandatory Pre-Registration: Enforce a strict "No Registration = No Access" rule. This applies to all visitors, contractors, and crew.
- Identity Verification:
- Check official government ID (Passport, ID card, Seaman's book).
- Note: Ensure your team knows which IDs are valid (e.g., in Belgium, a driving license is not an official ID).
- Real-Time Attendance: Maintain an up-to-date list of exactly who is on site (IN and OUT registration is mandatory).
- Action: Implement an anti-passback system on turnstiles to prevent badges from being passed back to others.
Pillar 4: Authorization
Access Control is checking the ID; Authorization is ensuring the legitimate business reason to be there.
- Define "Authorized": Access is subject to a specific business purpose, time, and place. If a person is not there for a specific job right now, they are unauthorized.
- Personal Badges: Enforce strict rules that badges are personal. Co-drivers cannot enter on the driver's badge; they must be individually authorized.
- Access Levels: Differentiate between internal staff and external visitors. Do not give permanent access rights to contractors who only visit occasionally.
- Action: Audit your badge list. Delete inactive users (e.g., those who haven't entered in 2 months) to prevent "ghost" access.
Pillar 5: Rail
Rail entries are often the weakest link due to the necessary gaps for tracks.
- Gap Protection: Install metal bars or concrete blocks at the bottom of the rail gate to prevent crawling under the tracks.
- Active Surveillance: The gate should only open when a train is approaching and close immediately after it passes. If it must remain open, it requires constant physical or CCTV surveillance.
- Pre-Registration: Receive wagon and goods information before the train arrives.
- Action: Verify that your CCTV covers the "blind spots" that a long train creates when entering the facility.
Pillar 6: Vehicle Control
Prevent vehicles from being used to smuggle unauthorized persons or materials.
- Registration: Log the time, driver, license plate, and country for every vehicle entering.
- Cargo Inspection: Conduct 7-point inspections on containers (Undercarriage, Doors, Right/Left sides, Front wall, Ceiling, Floor).
- Seal Verification: Check seals against loading documents. If a seal is broken, deny entry and report to the PFSO.
- Action: Create a separate "check zone" so that vehicle inspections do not block the main flow of traffic.
Refer to the full checklist in the Further Reading section below for even more detail!
5. How Should I Start?
We know, looking at the full scope of ISPS compliance can feel overwhelming.
Many facilities are lagging behind on these updates simply because the Capital Expenditure (CAPEX) and manual labor required to overhaul physical infrastructure is massive.
So why not flip the script?
Start with a fundamental security question: Do you actually know who is on your site or port terminal right now?
The Recommendation
Securing your digital perimeter, ie. the Access Control and Authorization pillars is the fastest, most impactful way to close the security gap without waiting for a multi-year infrastructure budget.
Start with certainty. This is where 9ID fits in. We offer a streamlined, automated solution to handle essential identity verification and authorization, allowing you to lock down your digital perimeter immediately. It is a high-impact, low-friction starting point compared to the massive scope of physical construction.
BIG PLUS: For our Belgian partners, 9ID is already integrated with AIGIS. This means you can plug directly into the national security grid from day one.
ISPS compliance is necessary, and it's never too late to get started.
So start with the most vital step: knowing exactly who holds the keys to your gate.
Find out how 9ID can help you work towards ISPS compliance!
6. Further Reading
- Belgian ports join forces for integrated port security | Port of Antwerp-Bruges
- Hundreds of Antwerp port employees suspended after drug screening | VRT
- Belgium launches 'AIGIS' system to monitor port bans more efficiently | The Brussels Times
- Belgium unveils new database to tighten port security and block criminals | Belga News Agency
- Paul Van Tigchelt | LinkedIn Post
- Koppeling AIGIS-Alfapass maakt havenverboden automatisch afdwingbaar | Flows
- The solution - Vertrouwensketen | Secure Chain
- René de Vries: ‘Secure Chain makes the port more resilient’ | Secure Chain
- HHLA and passify digitalise truck handling at Hamburg terminals | Port of Hamburg
- PASSPORT - Operational Platform managing a fleet of semi-autonomous drones exploiting GNSS high Accuracy and Authentication to improve Security & Safety in port areas | EUSPA
- The PASSport Project: Enhancing Safety and Security in European Port Areas through Drone Operations | M3 Systems
- Handbook ISPS | Port of Antwerp-Bruges
- ISPS - Port security standards and recommendations | Port of Antwerp-Bruges








